Aloha POS master terminal
 Point-of-Sale (POS) devices are an essential part of modern life; the blood line for merchants. As plastic payment cards have become the default payment method, the security of POS devices has become more crucial. I was interested in learning how real-world POS machines maintain security but “close examination” without the owner’s consent is a crime. I have no friends in business using POS devices, so I decided to order a used device for investigation. The Aloha Sharp pos terminal up-v5500 series manual is known to be very popular in the hospitality sector. (Figure 1)
Point-of-Sale (POS) devices are an essential part of modern life; the blood line for merchants. As plastic payment cards have become the default payment method, the security of POS devices has become more crucial. I was interested in learning how real-world POS machines maintain security but “close examination” without the owner’s consent is a crime. I have no friends in business using POS devices, so I decided to order a used device for investigation. The Aloha Sharp pos terminal up-v5500 series manual is known to be very popular in the hospitality sector. (Figure 1)
Figure 1 Aloha!
With Aloha Sharp pos terminal up-v5500 series manuals, usually there are multiple Front-of-House (FOH) terminals and a single BOH (Back-of-House) file server. The terminals act as the servers’ access point, allowing for direct interaction to input new orders, swipe credit cards and print receipts.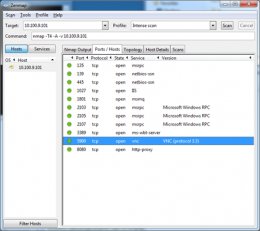 All transactions are logged and saved to the Aloha file server, which performs End-of-Day (EOD) transactions each day.
All transactions are logged and saved to the Aloha file server, which performs End-of-Day (EOD) transactions each day.
Figure 2 Typical architecture of Sharp pos terminal up-v5500 series manuals with Aloha
The system I acquired happened to be a master terminal (terminal 1) and would not normally operate without an Aloha file server on the same network.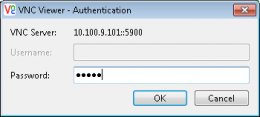 However, there is a fallback mode available where all transactions are handled offline, allowing the terminal to continue to accept orders and process transactions. I performed a lightweight pen-test of the system using that mode.
However, there is a fallback mode available where all transactions are handled offline, allowing the terminal to continue to accept orders and process transactions. I performed a lightweight pen-test of the system using that mode.
Port scanning
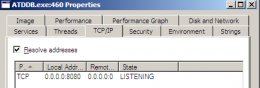
Figure 3 shows the results from NMAP scanning. I found file sharing related services (135, 139, 445), other MSRPC services (1801, 2103, 2105, 2107), and a VNC service running on port 5900. Interestingly enough, there is also a web server running on port 8080.
Figure 3 NMAP Scan result
VNC security
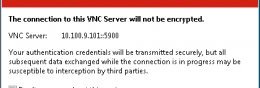
The first step in my pen-testing was to try to guess the VNC password. Ideally, passwords should be really difficult to guess, otherwise, you defeat the whole purpose of a password system (i.e. ‘something you know that other people don’t’). The first guess I made was so obvious (‘aloha’), but guess what? The password was correct – and I got access to the system on my first try.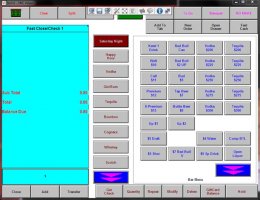 Moreover, this connection isn’t encrypted (Figure 5) so attackers with access to the infrastructure between the VNC client and the POS may be able to sniff the traffic.
Moreover, this connection isn’t encrypted (Figure 5) so attackers with access to the infrastructure between the VNC client and the POS may be able to sniff the traffic.
Figure 4 VNC login screen
Figure 5 Unencrypted VNC connection
When you login to the terminal through VNC you may see a screen similar to that shown in Figure 6. You can minimize the POS program, access an Explorer program and perform additional attacks.